When we make our repositories public or make changes to public repositories, GitHub's advanced secret scanning feature is triggered.
Within minutes you will get an email from AWS about the breach and your access key would have a quarantine policy attached to it.
👉 Key takeaway:
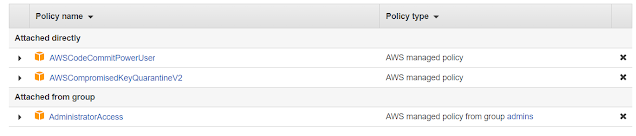
Furthermore, due to this feature of GitHub aws detects any exposed/compromised keys online, and will attach the "AWSCompromisedKeyQuarantineV2" AWS Managed Policy ("Quarantine Policy") to the IAM User of which keys are exposed, and trigger a mail notification to your registered account with the details. So every time you try to use any resources from the exposed key you will get an authorization error.
FAILED! => {"changed": false, "msg": "Instance creation failed => UnauthorizedOperation: You are not authorized to perform this operation. Encoded authorization failure message: mw4pJJXTCly9BRXiEEzZhmPvanjwTNMCJ0MRAsFGw-jSRJyUwRz9tgdKjQF_S_d3IspWq_d4-LL1The "UnauthorizedOperation" error indicates that permissions attached to the AWS IAM role or user trying to perform the operation does not have the required permissions to launch EC2 instances. Because the error involves an encoded message, use the aws-cli to decode the message.
Encoded-message is the encrypted value you get in your error msg $ aws sts decode-authorization-message --encoded-message encoded-message
No comments:
Post a Comment